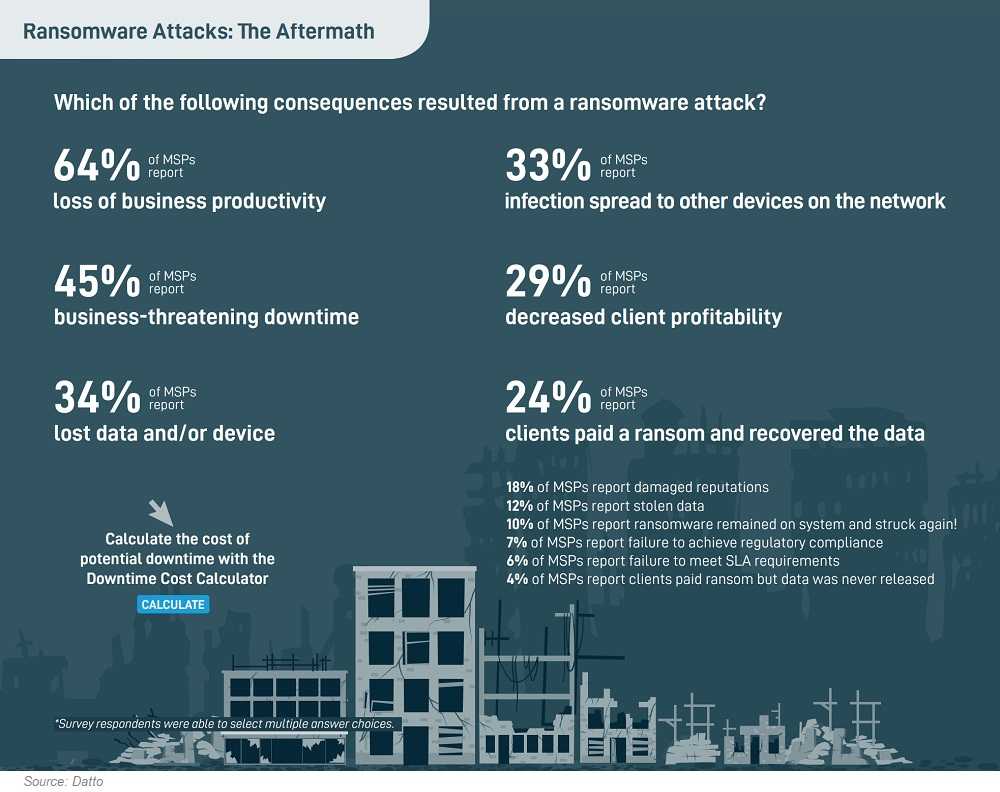
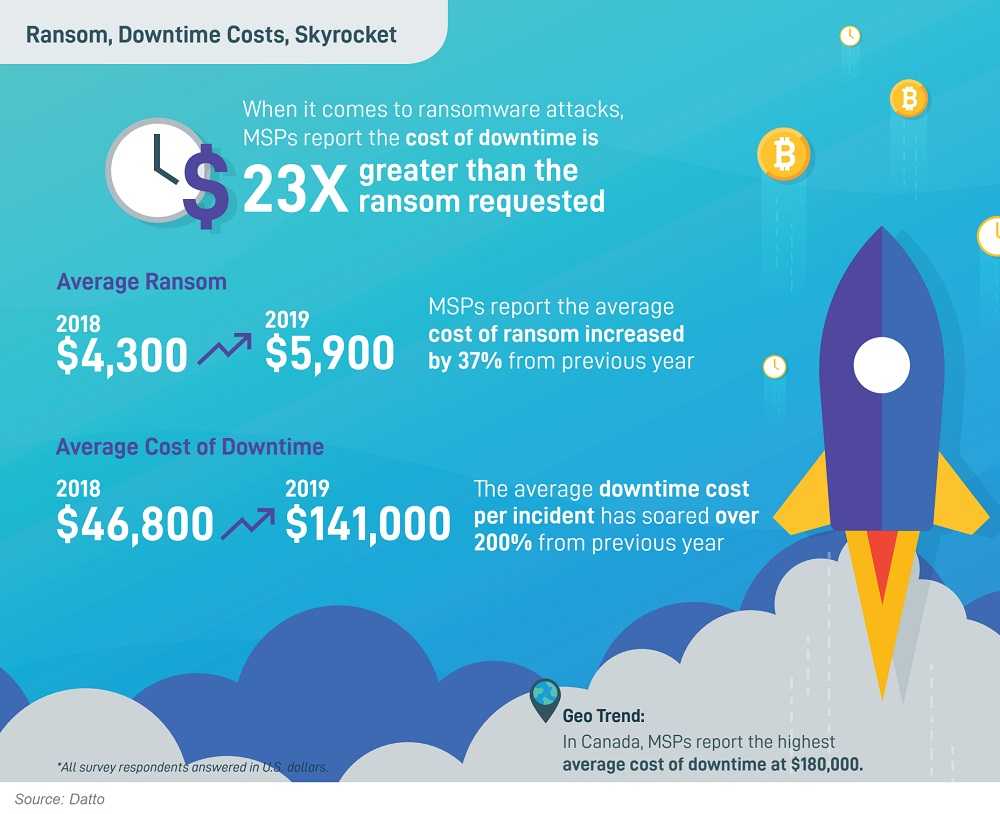
The data breach headlines normally focus on mega breaches involving huge corporations and their many customers. The reality is, many small-to-medium sized businesses (SMBs) suffer data breaches that don’t make the headlines, but are still an epic security event for the enterprise and its customers. From ransomware attacks to other malware infections, each SMB has a need for their own customized data security plan.
SMB Security Statistics
If you’re a new or established SMB owner, here’s one statistic that should resonate with you: 60% of SMBs are out of business within 6 months of a data breach. Other stats include a 424% increase in SMB cyberattacks in 2020; 92% of malware is delivered via email; and incredibly, 60% of SMBs believe a cyberattack won’t happen to them.
Every SMB can achieve their own effective information security program. It’s not impossible. Following are some tips.
Starting Your SMB Information Security Program
A solid security program begins with building from the ground-up or re-tooling an already existing plan. Each program should include deploying security tools to effectively monitor and protect company data and network assets, as well as creating the policies and processes surrounding that protection. A good plan should first and foremost protect the company’s data.
Even though your security plan may involve outsourcing services for monitoring and protection to an expert consultant or Managed Security Service Provider (MSSP), ultimately the SMB is responsible for defining the policies and processes guiding outside assistance.
SMB Framework for Cybersecurity
Using security frameworks are the best way SMBs can organize a cybersecurity program. Assistance is available for from the Center for Internet Security, International Organization for Standardization, and the National Institute of Standards and Technology.
To ensure you information security program succeeds, include the staff. Every employee, from CEO to administrative staff, must understand their part and adhere to the plan. The following guideline format helps achieve that goal.
Employee Awareness Training for every level staffer. Regular education about security risks, especially email phishing, is recommended. Don’t count on doing this once a year and forgetting it. This is an ongoing effort. Everyone should be able to identify phishing and other hacking tactics, and their education is a critical part of a successful plan.
Objective behind your data security program. Other than protecting data, questions like why data access is limited and what assets are valuable should be answered and explained.
Written policies about working on personal devices, working remotely, using unauthorized IT, and storing data on non-company devices should be clearly spelled out. They should also be enforced.
Responsibility for monitoring security needs be clear. Determining who’s responsible for security oversight, such as working with security vendors, MSSPs, monitoring data, and more, should be identified.
Having an information security program is an investment in the success of the business, including its future.
/HarborNetworksLogo-1.png?width=319&height=76&name=HarborNetworksLogo-1.png)