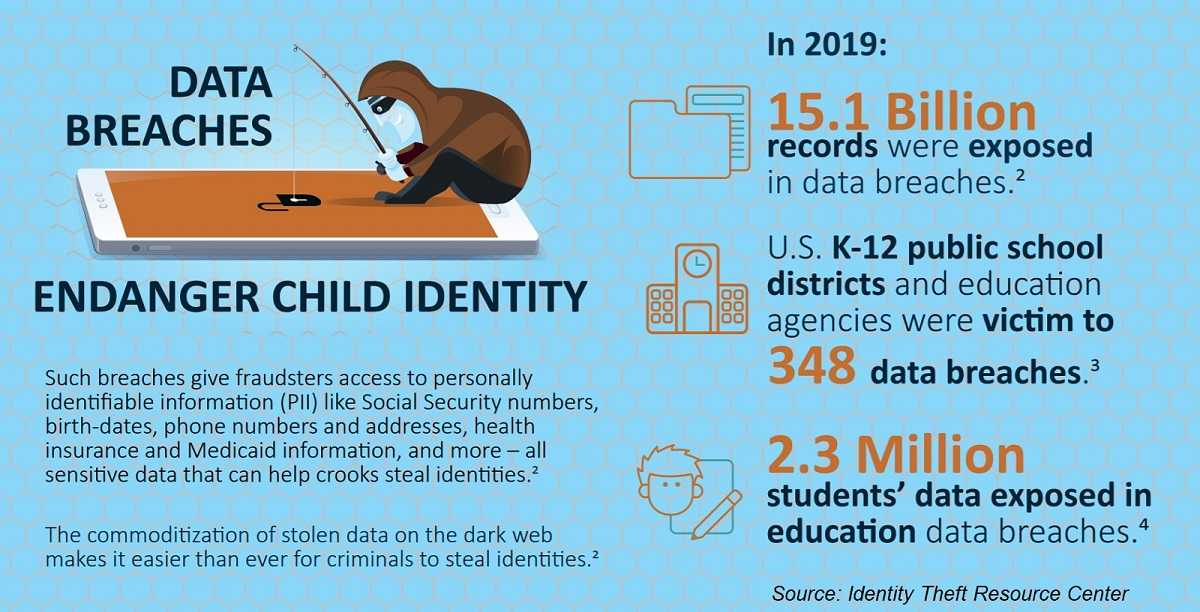
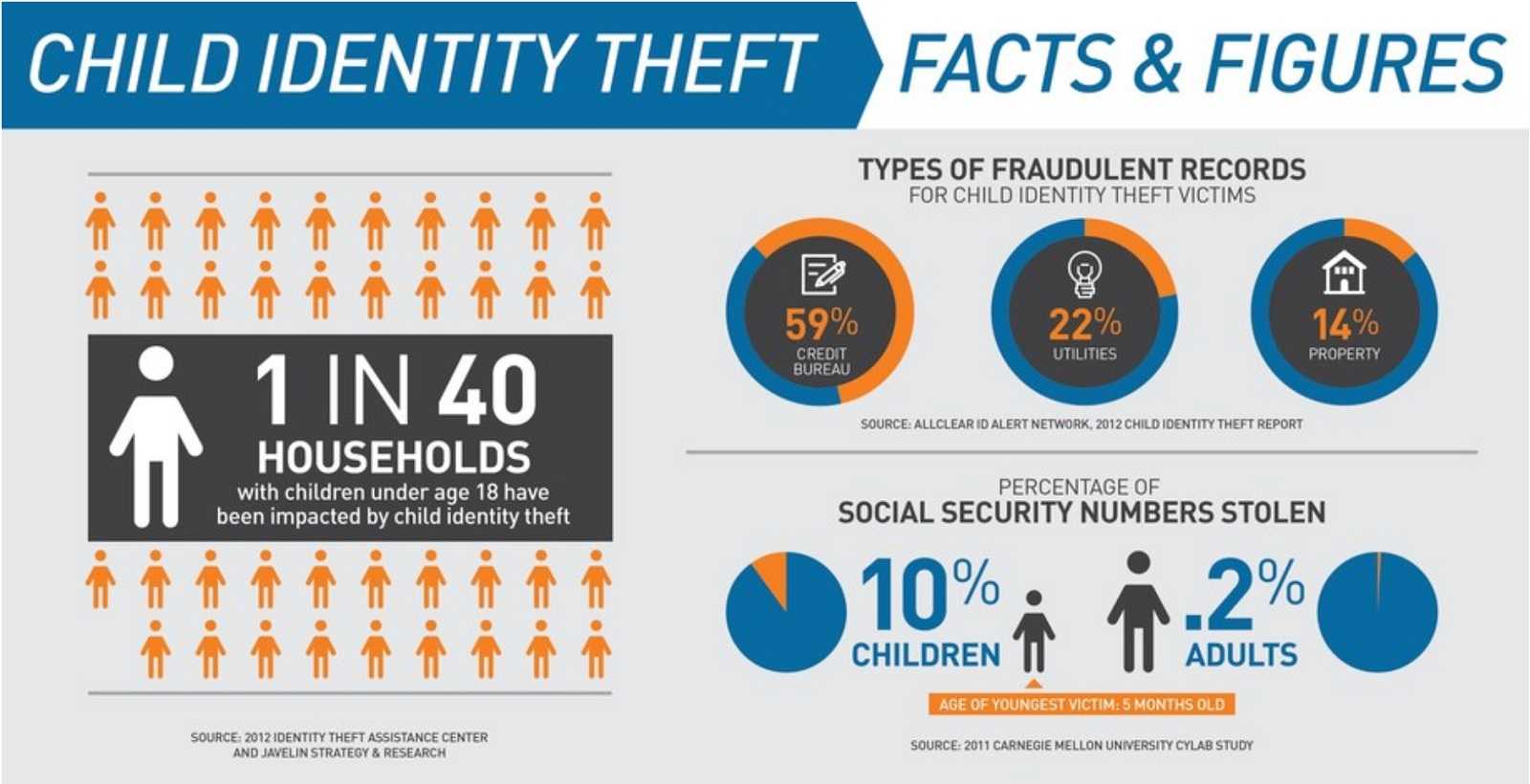
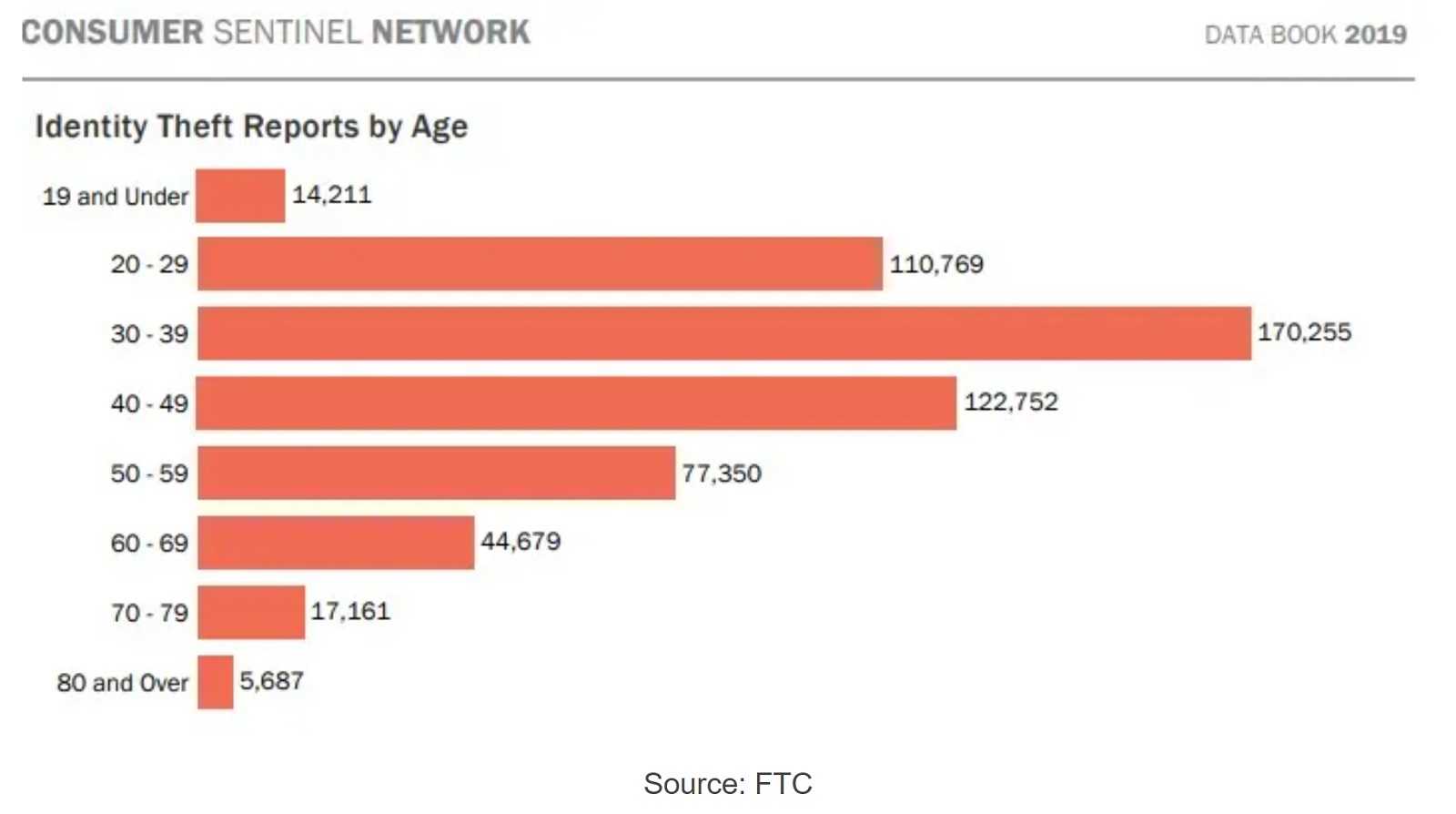
Adults should be well-aware of hacking and the risks involved when traversing online. But what many don’t know is the sad truth that children are also targets of online abuse. Sadly, this includes infants. The good news is that parents aren’t helpless when it comes to protecting their child’s online activities and real-world identities. Knowing the signs of child identity theft, other harmful vulnerabilities and how you can help prevent them is a great way to start.
Signs of Child Identity Theft
Problems will start popping up, with some starting earlier on, and others after it’s too late. If you start receiving mail in your child’s name, there’s absolutely reason for concern. That’s a sure sign your child’s name, address, and more have potentially been stolen. In particular, getting mail from a bank or credit card company tells you their identity and possibly their Social Security number and more have been compromised.
The first task in the action plan is to check the credit reports for the child. Contact Equifax, TransUnion, and Experian to make sure their information isn’t being used to obtain credit. One from each company is available per year FOR FREE. Even if there isn’t an immediate reason for concern, checking is not a bad idea.
Below are some of the most common hacking scenarios affecting children, along with ways to stop these crimes in their tracks before any real damage is done.
PROBLEM: Too much information. Identity theft can happen when too much PII (personally identifiable information) about a child is posted online, no matter their age. The younger a child is, the more difficult it may be to know if their identity has been compromised.
ANSWER: Posting details about children is risky. Hackers cobble that information together to create a viable target, and the more PII, the bigger the crime. Children have clean records, and cybercriminals can open credit card accounts, take out loans and purchase big-ticket items in your child’s name. This abuse could go on for years before being discovered. Consider taking a further step to freeze your child’s credit as it will prevent others from taking advantage.
PROBLEM: Posting Photos. As much as parents want to show their family and friends their adorable children, posting photos online is also risky. It’s called digital kidnapping, where someone easily steals a child’s photos, gives them new identities, and then pretend the child belongs to them. As far-fetched and disturbing as it is, it happens more than people realize.
Even worse, posting their photos also leaves a child vulnerable to pedophiles. These predators share stolen photos on pedophile and sexual abuse sites. These innocent photos can be manipulated into appearing sexual and then posted on child pornography sites.
ANSWER: Check your account privacy settings and make sure only trusted friends and family are able to see the posted photos and what you share about them.
PROBLEM: Social Media Apps. Children using social media apps are vulnerable to communications from those with bad intent. These creeps start with friendly chatter that spirals into intrusive and dangerous posts. Some are grooming the child for “cat fishing,” a way to gain their trust. Once done, their posts can go downhill fast, including sexual messages and attempts to get the child involved in pornography. It can also result in real life meetings between the child and the predator.
ANSWER: Take control of your child’s social media settings. Make sure they are set on private, disable geotagging that shows the exact location of your child, and configure parental controls on your family computer. Having a discussion with your child about the risks of sharing PII and photos is wise, but keep it on a level they can understand and won’t end up traumatized.
PROBLEM: Phony Gaming Apps. Kids love online gaming, and that opens a world of potential child abuse they have no idea exists. Hackers use these fake apps and lure children into downloading them. The apps contain malicious software designed for spying that steals login information, account details, and allows remote access to a device. The fake apps can also redirect a child to a malicious, inappropriate website under the control of the hacker.
ANSWER: Be sure your child downloads apps only from the official stores for their devices. They screen apps for malware, which third-party sites do not always do diligently. Make sure to activate restrictions that require your password for purchases and downloads and use parental controls on the family computer.
PROBLEM: Gaming Chatter. Those online game consoles a child goes bonkers for, like PlayStation, Nintendo, and Xbox, can unfortunately put them at risk. Gaming predators are out there, and they use the in-chat function of the game to establish communications with children. They appear to be another child playing the game to gain their confidence. Once done, they can initiate requests for personal information, sexually explicit photos and videos, and in-person meetings.
ANSWER: You can prevent your child from harmful chatter by limiting communication and content, and by setting playtime limits. This will keep your child from interacting with other players, including those with bad intent. They won’t be able to chat with other players, including messages and game invitations.
IN A WORD: Control. Having control over your child’s online activities is paramount to keeping them safe. They may not be happy about it, but that’s truly little compared to their online safety. Keeping settings to the most private gives you even more control over their well-being. Also, know that your own online activities such as posting too much about them can also put your child at risk. Regular discussions about the risks of their online activities will benefit parents and children alike.
/HarborNetworksLogo-1.png?width=319&height=76&name=HarborNetworksLogo-1.png)