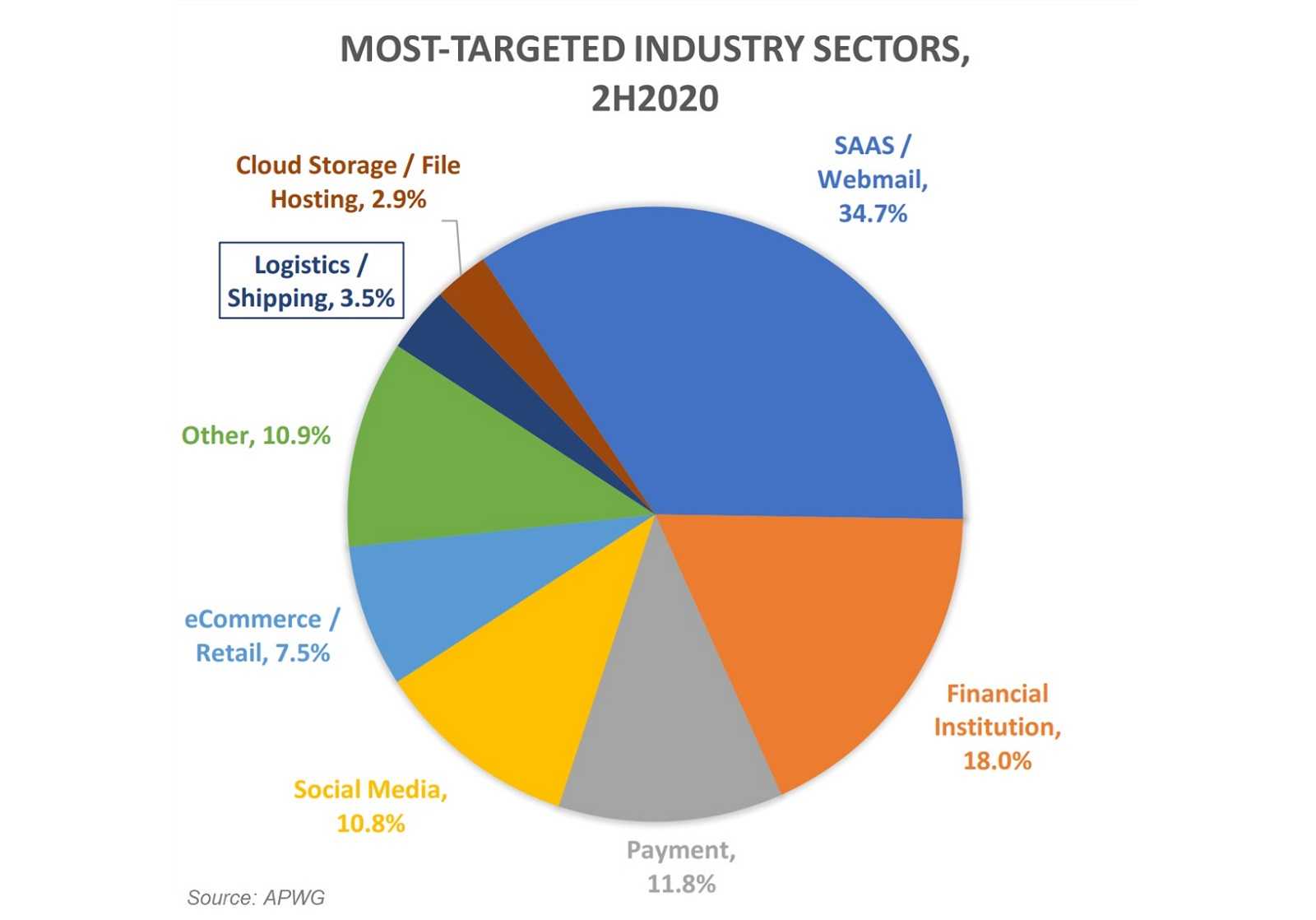
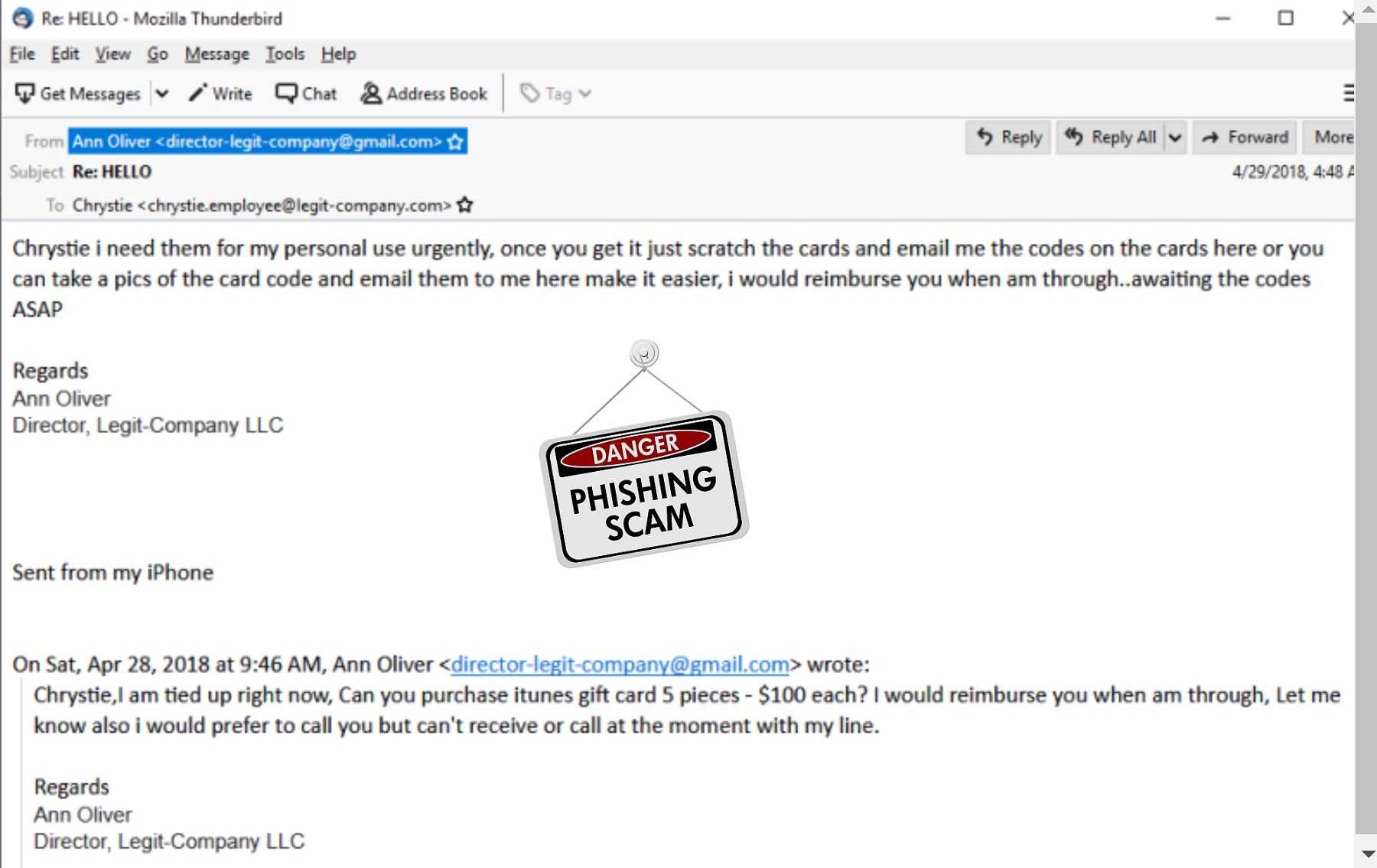
When does buying gift cards for employees turn into a business email compromise attack? The simple answer is “when hackers are behind a gift card BEC scam.” Business email compromise (BEC) can be devastating to any company, especially when 60% of small-to-medium-sized businesses don’t survive these assaults. However, BECs target a wide range of victims, and it’s reported that hackers use gift card scams in 66% of their email phishing attempts. The importance of avoiding BEC scams can’t be overstated, and what helps protect against these cybercrimes should be of interest to employees and CEOs alike.
According to KDMARC, an email security company, last year’s losses from BEC scams totaled nearly $80,000 per attack. Since email phishing is the starting point on the road to success for BEC hackers, they’ve sharpened their skills over time, making the emails more effective and more likely to be successful.
What a BEC Gift Card Scam Looks Like
An innocent email from a CEO to their assistant requesting they purchase a number of gift cards to reward employees with, can go south quickly. Responding to the email request to the CEO that includes the gift card codes as proof of purchase gets a quizzical response from them, asking why the gift cards were purchased to begin with. Surprise! You’ve just been duped into being the target of a successful BEC scam.
The FBI’s Internet Crime Complaint Center (IC3) found the price tag for BEC losses last year totaled $1.8 billion. Many of these attacks can exceed the cost of gift card scams, with many BECs involving bogus requests for substantial wire transfers that can leave a considerable dent in a company’s bottom line.
Protect Against BEC Attacks

- Employee cybersecurity training on a regular basis helps staffers identify email phishing and other types of attacks. That includes those emails that are socially engineered to target specific employees, especially those working directly with finances. Since attacks trend, evolve, and improve over time, employee education should be more than just once a year and involve every level of staff, including CEO’s.
- Approach every email with a healthy dose of skepticism, no matter whom the sender claims to be. Always verify requests involving finances with the sender and at least one other employee.
- Listen to your instincts. If your Spidey-sense is triggered by an email, trust your suspicions. Treat the email as potentially harmful and report it to IT whenever possible.
- Always follow your company’s procedures, even if an email request is presented as desperately needing to be rushed. A time-sensitive, rush request for action should always be scrutinized.
- Always report any email you suspect, or know, is phishing. Doing so makes others aware of the email scam, including BECs, and can be a learning opportunity for others.
/HarborNetworksLogo-1.png?width=319&height=76&name=HarborNetworksLogo-1.png)