Through our partnership with leading cybersecurity readiness provider GreyCastle Security, we are able to provide our community with industry leading content, which is sourced below
Today’s business climate is complex. The cloud, Software-as-a-Service (SaaS), mobility, outsourcing and third-party service providers has increased efficiencies, conveniences, and profits for businesses globally. These same advancements have introduced
new cybersecurity risks and challenges to any organization working beyond their four walls.
Whether you are required to assess the risk of your third parties, or you are buried in vendor risk questionnaires, Vendor Risk Management is the solution.
Vendor Risk Management has become a critical function for any business that utilizes third parties for critical business functions.
VULNERABILITY ASSESSMENT
What is a Vulnerability Assessment?
Vulnerability scanning has become a cybersecurity staple. Utilizing one or more "scanning" tools, your entire infrastructure(s) can be scanned for technical vulnerabilities. There are many reasons to do this:
-
-
-
Match up critical vulnerabilities with critical assets
-
Generate a list of the patches or other remediation that need to be applied
-
Identify (through the assessment process) all of the false-positives and false-negatives that exist
-
Satisfy PCI, HIPAA and NERC-CIP regulatory requirements
-
-
PENETRATION TESTING
What is a Penetration Test?
A Penetration Test, often called "red teaming" or a "red team exercise" is the practice of simulating as closely as possible the effect that cyberthreats could have on your business. It is a simulation of a real-world attack on targeted assets using the same tools and techniques that modern criminals use. This is done by understanding who your threats are, their capabilities, motivations and targets and "hacking" your systems the way they can.
Many so-called "cybersecurity companies" have done a good job of confusing buyers and generating interest in Penetration Testing. This is because breaking things is easier than fixing them, and they aren't very good at fixing things.
Types of Penetration Tests:
There are many threats to your business, understanding who they are will help you conduct a good Penetration Test. Understanding their motivations, resources and targets will make it even better. We help with all of the above. Nearly all threats will fall into one of the following categories:
-
-
-
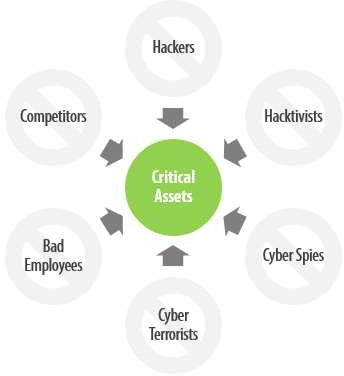
Scenario-Based Test - Simulation of a specific threat or threat sources, depicted by the scenarios illustrated here.
-
Target-Based Test - Focused testing of a specific application, subnet, location, people or other assets, typically considered "purple "
-
Advanced Persistent Test - An extension of a Scenario-Based Test over a prolonged period of
-
-
Penetration Testing vs. Vulnerability Assessment:
What's the Difference?
This infographic explains everything you need to know about vulnerability assessments and penetration tests, including the different functions of each, why you should perform them, and what you need to consider when deciding which is right for your organization today.
|
Function |
Vulnerability Assessment |
Penetration Test |
|
Identification of ALL Technology Vulnerabilities |
x |
|
|
Analysis of False-Positives and False-Negatives |
x |
|
|
Vulnerability Scanning |
x |
OPTIONAL |
|
Full Interaction with Client Team |
x |
|
|
Limited or No Interaction with Client Team |
|
x |
|
Social Engineering (Phishing, Vishing, Smishing) |
|
x |
|
Targeting of Critical Assets |
|
x |
|
Exploitation of People, Process, and Technology |
|
x |
Which one should you do? The answer is probably "both", depending on the problem you're trying to solve, the maturity of your cybersecurity controls and your regulatory obligations.
/HarborNetworksLogo-1.png?width=319&height=76&name=HarborNetworksLogo-1.png)
