In these uncertain times, staying smart about personal health is necessary to fight coronavirus (COVID-19). But we also need to stay smart about cybersecurity. True to form, cybercriminals are doing everything they can to lie, cheat, and steal their way onto your device and into your personally identifiable information (PII). Stealing finances and identities are nothing new for hackers, but what is new is the voracious rate at which they are using COVID-19 as a cover for fraudulent activity.
A recent study by Check Point Research shows a 10x increase in the average number of new, registered domains since the end of this February. It also finds thousands of new websites are popping-up overnight with coronavirus-themed domains, and these are 50% more likely to be malicious. Hackers are capitalizing on COVID-19 virus fears with dramatically increased email phishing attacks, malware-laden attachments, and bogus links to compromised websites. At a time when people are vulnerable to deception, there’s one thing we can be sure of–cybercriminals are working overtime.
Many millions of users are relying on their devices for vital connections to family and friends, shopping, school, work, entertainment, and more. That means an abundance of cybercriminals are ready and waiting to dupe unsuspecting victims with their illegal schemes. Right now, COVID-19 website themes abound, with many promising trusted information to the public, and still others reassuring the purchase of products in high demand. These fake or “spoof” URLs abound, with many of them taking advantage of typo squatting, which happens when a user accidentally misspells a domain name. Below are some of the coronavirus-themed attacks that are currently circling the globe, as well as digital hygiene tips for you and your device.
COVID-19-Themed Attacks
- Malspam (malicious spam) campaigns are targeting finance, manufacturing, transportation, and pharmaceutical industries. One campaign exploits a Microsoft Office bug to install info-stealing AZORult malware on a system. This one uses a fraudulent version of the Johns Hopkins Coronavirus Map as an infected file. Other malspam offers masks and other health items for sale. Hackers take payments and send nothing in return.
- A virus-tracking theme called COVID-19 Tracker changes a smartphone’s lock-screen password, installs CovidLock ransomware and demands a $100 Bitcoin ransom to unlock the phone.
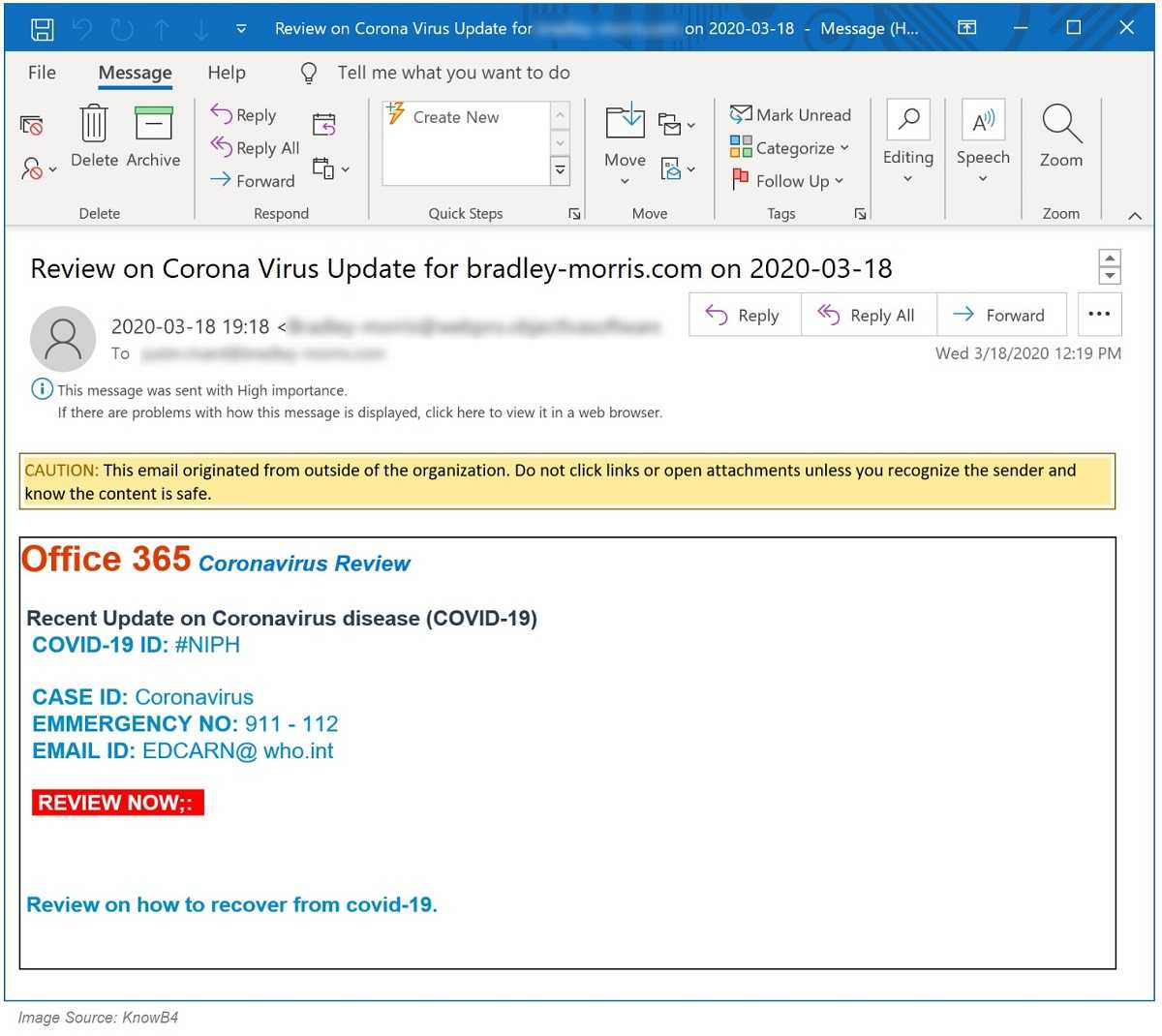
- Phishing campaign targeting students and university staff with fake emails requiring their Office 365 credentials and then stealing them.
What You Can Do: Digital Hygiene

- Use only trusted sites, such as official government websites for COVID-19 information. Never click an email link for any website and be sure to type-in the official site name yourself, using caution not to make typos.
- Beware emails and files from unknown senders. Bogus links abound in phishing emails and lead to fake sites that steal data, even though they may look legitimate. Always check the sender’s email address for authenticity, misspellings, and anything that looks suspicious or out of place. Avoid those emails asking for PII, passwords, and account numbers. Go directly to the site yourself to see if your PII is truly needed.
- Keep all devices and software up-to-date, including using anti-virus software. Make sure your device is always running the latest software, including applying system security patches as soon as they are available.
The cybersecurity landscape is changing rapidly, yet most businesses have the same security posture they had years ago. Today’s threats must be countered with behavior-based tools, in addition to traditional methods.
Harbor Networks helps businesses develop a future-oriented security strategy, rationalizing a security posture with a sensible budget, and creating business cases to support new initiatives.
Typical solutions include:
• Endpoint Protection Platforms (EPP) & Endpoint Detection and Response (EDR)
• Security Information and Event Management (SIEM) & Threat Detection
• Penetration Testing
• Secure Web & Email Gateways
• Zero-Trust
• Data Loss Prevention (DLR) & Cloud Access Security Broker (CASB)
• Firewall & Intrusion Detection Services (IDS) / Intrusion Protection Services (IPS)
• Secure Access Service Edge (SASE)
• Identity and Access Management (IAM)
• Cybersecurity Awareness Training
Businesses today must prepare for a cybersecurity incident. A balance of defensive and offensive measures is required to keep the organization safe and to detect security breaches as soon as they occur.
/HarborNetworksLogo-1.png?width=319&height=76&name=HarborNetworksLogo-1.png)